How a Web Monitoring Service Can Detect the Pakistani Banking Data Breach in Advance
Major banks across Pakistan have suspended use of their debit cards and blocked international transactions after a report that data from a total of 19,000 debit cards were stolen in a cyber security breach. Debit card details have been published in two separate dumps on the Darknet for sale.
That got us thinking. Can data breaches like these have been detected in advance, mitigating the damage done to over 22 different Pakistani banks and their customers? This could be significant, especially when you consider that according to some sources, it was the largest banking data breach in Pakistan’s history — a total sum of $6 million stolen from customers.
The First Signs of Trouble on the Dark Web
The truth is that with most data breaches, the hackers left trails of their attack in advance.
Hackers often publicize their plans in advance, especially when they are data leaks of major organizations — such as financial institutions. Analysts can track these threats through a web monitoring service, often piecing the data together over time to understand the story — or data breach — about to be announced.
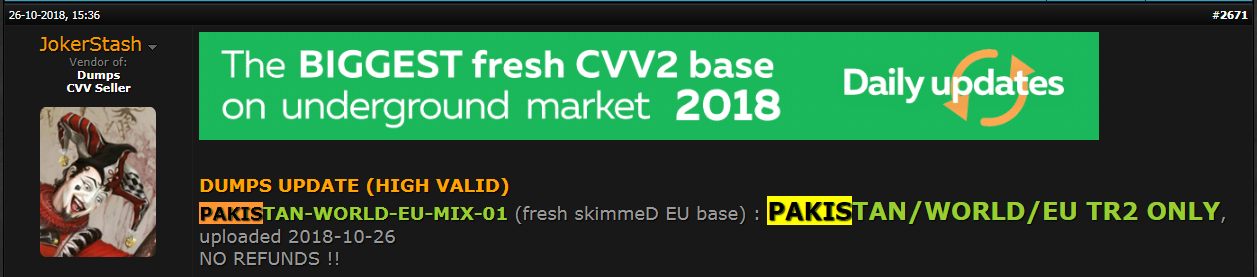
In the case of the Pakistan data breach, early signs were apparent. An actor by the name of JokerStash advertised his work as early as October 26th, which was an entire day before the first data breach was officially announced by Bank Islami.
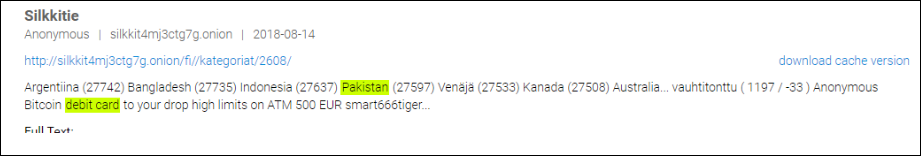
With continuous dark web monitoring, analysts can find even earlier references to the same data breach, like the one from as far back as August from Silkkitie, a TOR marketplace.
Two Data Breaches and Their Early Warning Signs
After the breach occurred, Pakistan’s Computer Emergency Response Team (PakCERT) revealed a list of 8,864 debit cards from 9 different banks that had appeared on the dark net for sale at prices between $100 and $150 each with the name PAKISTANWORLD-EU-MIX-1, hinting to the idea that there will be a second dump in the future.
A quick monitoring of the Dark Web by Webz.io shows that the actor JokerStash advertised his plans to release the first dump of credit card information as early as October 26 in the Club2CRD network. The Club2CRD network is a huge openweb forum dedicated to carding and leaked credit card information. JokerStash happens to be quite active in this forum.
JHe advertises the dump as the PAKISTANWORLD-EU-MIX-1, the same as the label PakCERT also found after publicizing the breach.
That’s an entire day before the first breach was officially reported.
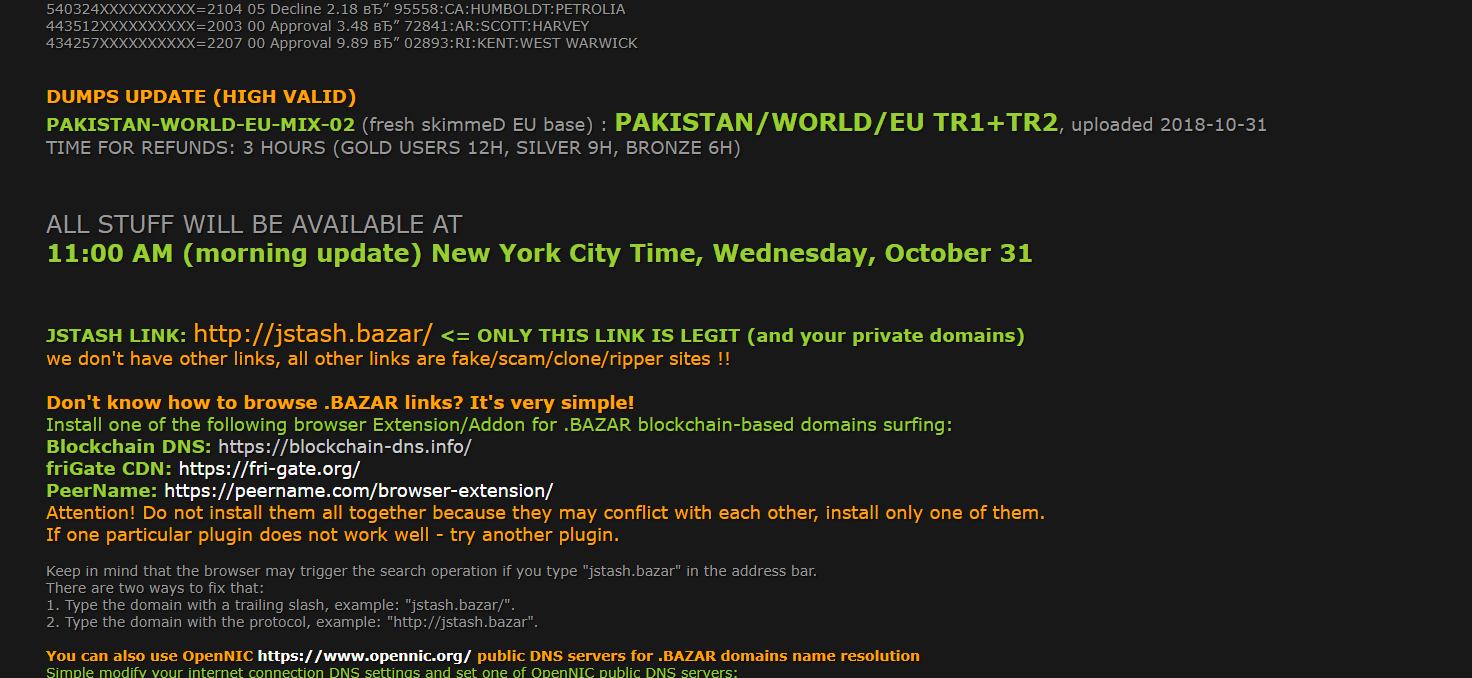
Unfortunately, that wasn’t all of the data JokerStash was planning on dumping. Notice that the dump was named PAKISTAN-WORLD-EU-MIX-02 and announced that it would be uploaded to the Dark Web on October 31, 2018, the same day that the second breach was reported. It was first advertised in the TOR network and later published in openweb and .bazar network.
What’s really crazy is that Webz.io was able to find a reference to this dump from as far back as October 26th in our repository!
The Importance of Continual Web Monitoring in Threat Detection
Financial institutions, with their incredible access to data such as credit cards and social security numbers, are at a huge risk for data breaches. Every organization has a critical responsibility to plan in advance to be able to execute an effective crisis management strategy in the case of a data breach or other type of security attacks. With a web monitoring service such as Webz, however, organizations can mitigate the damage done to financial institutions such as Bank Islami as well as stolen money from its tens of thousands of customers whose data was breached in the attack.
Want to learn more about how you can detect and monitor data breaches in advance with dark web monitoring? Check out Webz.io’s Cyber API now.